IDrive® BMR backup and recovery best practices
The IDrive BMR best practices guide is intended to be used as a to-do checklist by the IT admin managing the account for the business. It is also intended for professionals seeking suggestions on optimal management and the use of the IDrive BMR device. The guide is not intended to replace full documentations such as the user guide, FAQs, and the knowledge base but rather as an accompaniment to these documents.
IDrive® BMR documentations
The best-practices pointers are action-based and do not go into detail on the theories. For operations-related information, check out our full documentations.
| FAQs - Get answers to frequently asked questions on IDrive BMR |
Your queries are not answered here? Contact our 24/7 support for immediate assistance. You can also schedule a session with one of our technicians for assistance with device setup.
8 best practices for IDrive® BMR
Here are 8 practices for improving data protection with IDrive BMR:
1. Review backupsReview your backup logs and email notifications every alternative day to ensure all backups are working as expected. Monitoring logs and notifications help identify problems such as incomplete backups and other concerns at an early stage. Where?
View all the activity logs under Logs and manage your backup notifications under Settings > Mail > Backup notification. 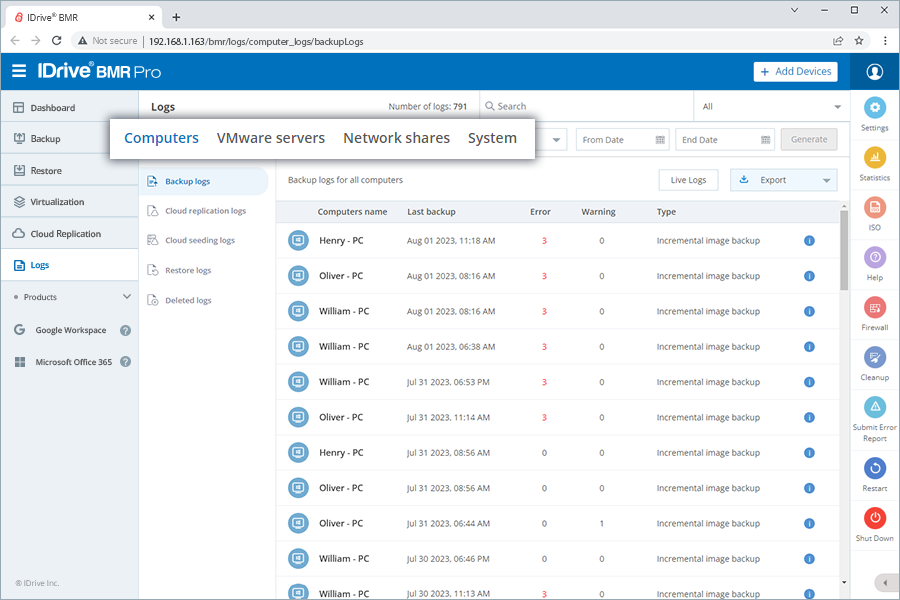
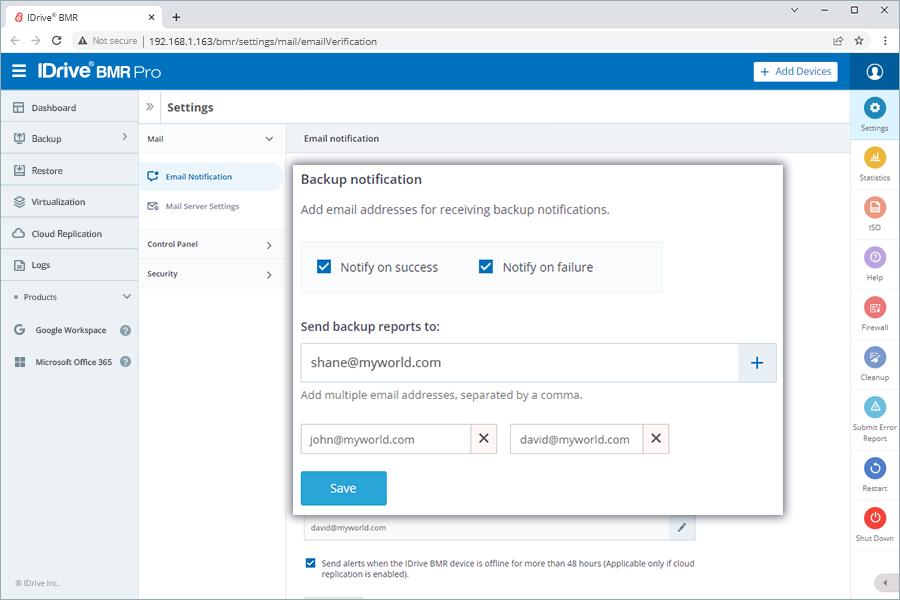
|
2. Restore data, as neededRoutinely perform data restores — file recovery, bare-metal system recovery, and virtual instances that are disconnected from the core network. Recovery via file restore and virtualization is recommended once or twice every week. Where?
Manage data recovery under Restore and Virtualization in the IDrive BMR device interface. 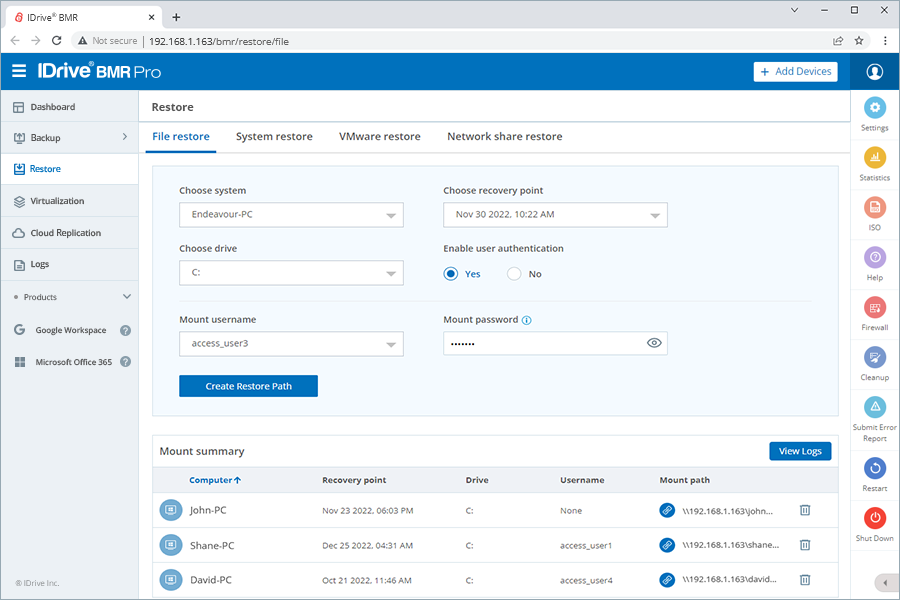
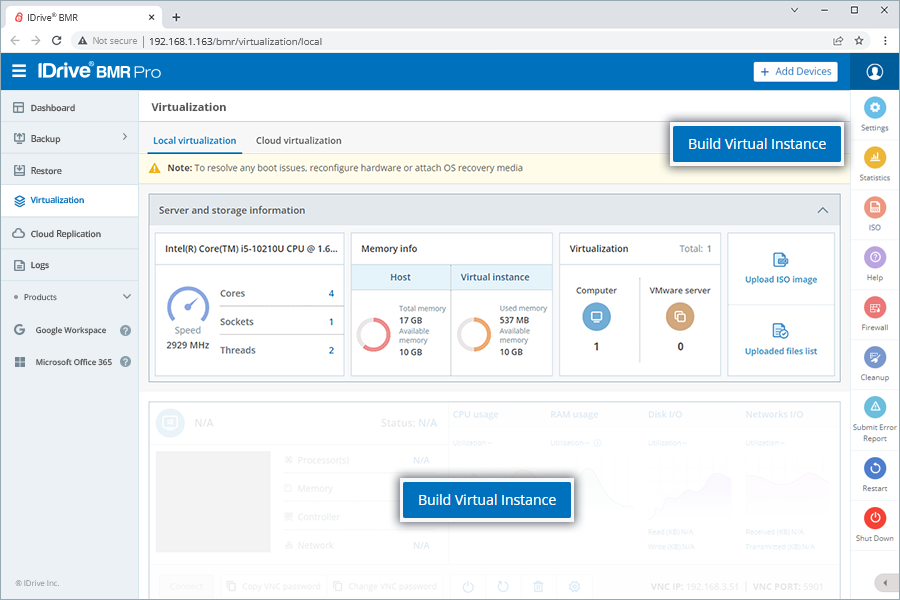
|
3. Monitor storage utilizationConfigure the retention settings to suit your business recovery plan and avoid over-utilization of the IDrive BMR storage. Where?
Navigate to Backup > Computers > Settings and edit the Retention settings field. Use the slider to set the minimum and the maximum number of image backups the device should retain for a computer. The old backups will be removed during the cleanup operation. 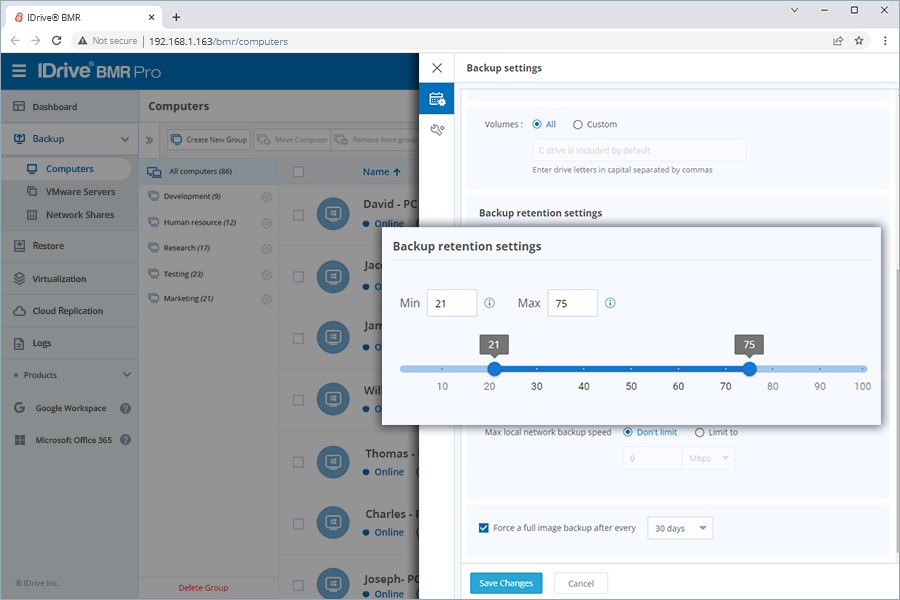
|
4. Monitor system health statusMonitor the health of the RAID and OS hard drive every alternative day to ensure your business data is protected at all times. Where?
Go to Statistics > System health for comprehensive information on RAID and OS drive health status. 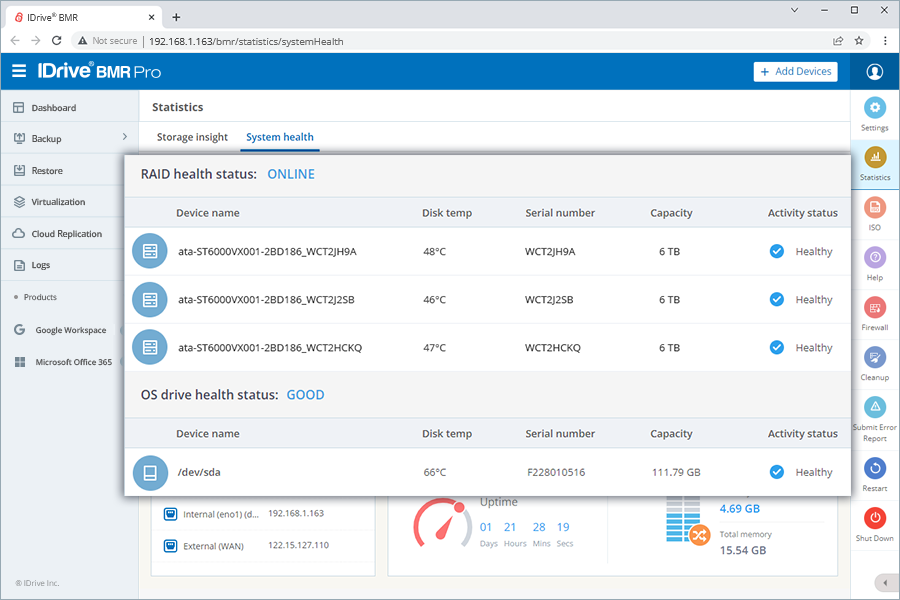
|
5. Optimize automated cleanupOptimize the cleanup of old backups in the local storage by suitably configuring the global filesystem quota or storage-utilization limit at 80% or lesser. Where?
Click Cleanup and configure the Global filesystem quota or the storage utilization limit upon reaching which the device will initiate a cleanup. 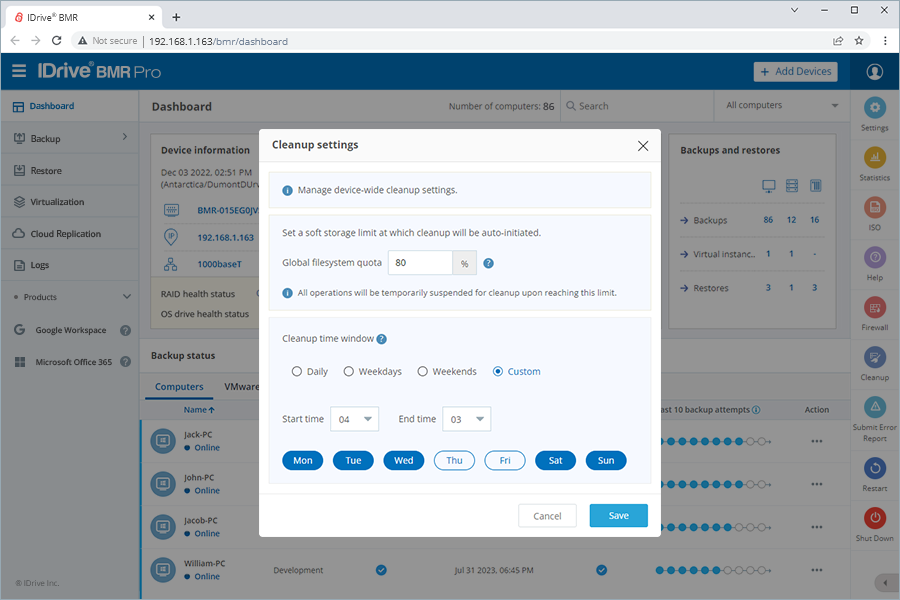
|
6. Monitor the firewall restrictionsRun a firewall check on the IDrive BMR device to ensure all the ports needed to run the services are open. Refer to firewall details. Where?
On the RHS menu, click Firewall and run a firewall check for general, mail relay server, cloud replication, and remote manage configurations. 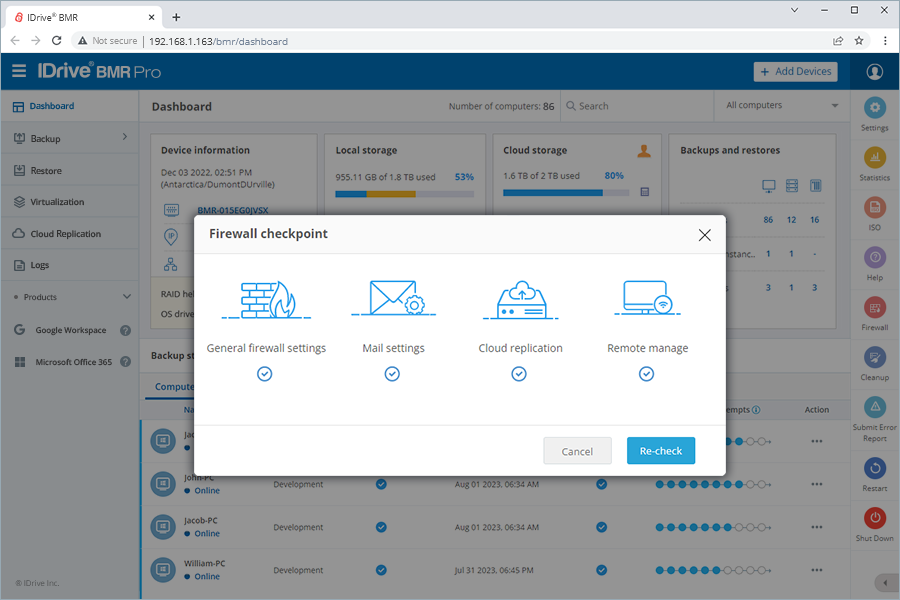
|
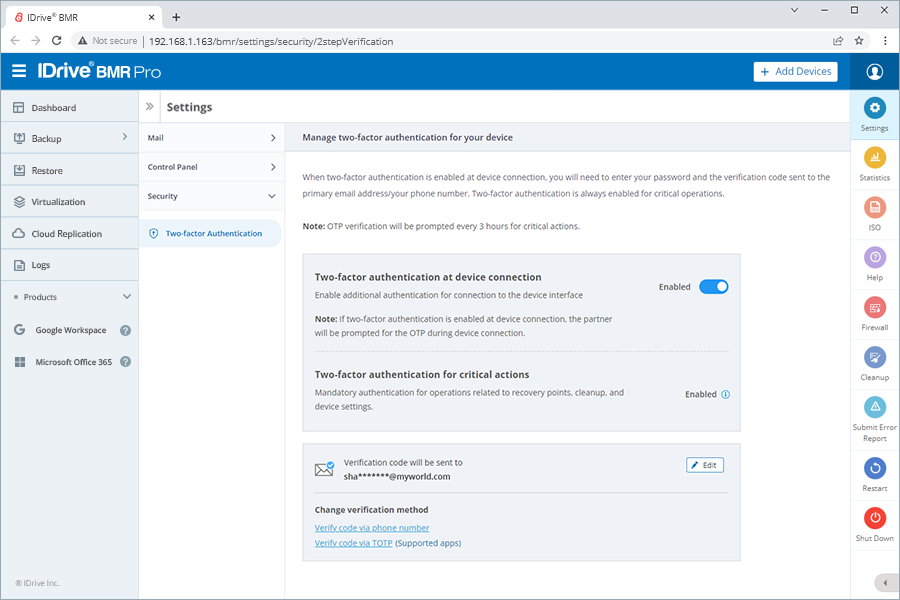
7. Secure the device interface with 2FAEnable phone number/email address/TOTP application on your mobile device based two-factor authentication to prevent unauthorized access and secure the connection to your device. Where?
|
8. Maximize uptime with Uninterruptible Power Supply (UPS)The IDrive BMR device is enabled with the resilient feature to automatically power-on after a power failure, ensuring continuous operation and reliability. However, to enhance the robustness of the device and provide an additional layer of security against power disruptions, we highly recommend integrating an Uninterruptible Power Supply (UPS) with your IDrive BMR device. |
Data security protocols
IDrive BMR is dedicated to safeguarding your data within our platform.
- We ensure device interface security through mandatory two-factor authentication and one-time password verification for various operations such as deleting recovery points, deleting network shares, removing machines, performing manual cleanup, updating primary email address, changing password and updating time zone.
- Two-factor authentication can be applied at device connection to ensure user authentication.
- Additionally, we verify trusted devices for downloads and enable password authentication for data deletion in the web console.
These comprehensive security protocols ensure that your data remains secure while using our services.